內容目录上一个主题< 过滤与清理(Filtering and Sanitizing) 下一个主题本页 |
上下文编码(Contextual Escaping)¶Websites and Web applications are vulnerable to XSS attacks, despite PHP provides escaping functionality, in some contexts those are not sufficient/appropriate. Phalcon\Escaper provides contextual escaping, this component is written in C providing the minimal overhead when escaping different kinds of texts. We designed this component based on the XSS (Cross Site Scripting) Prevention Cheat Sheet created by the OWASP Additionally, this component relies on mbstring to support almost any charset. To illustrate how this component works and why it is important, consider the following example: <?php
//Document title with malicious extra HTML tags
$maliciousTitle = '</title><script>alert(1)</script>';
//Malicious CSS class name
$className = ';`(';
//Malicious CSS font name
$fontName = 'Verdana"</style>';
//Malicious Javascript text
$javascriptText = "';</script>Hello";
//Create an escaper
$e = new Phalcon\Escaper();
?>
<html>
<head>
<meta http-equiv="Content-Type" content="text/html; charset=utf-8"/>
<title><?php echo $e->escapeHtml($maliciousTitle) ?></title>
<style type="text/css">
.<?php echo $e->escapeCss($className) ?> {
font-family : "<?php echo $e->escapeCss($fontName) ?>";
color: red;
}
</style>
</head>
<body>
<div class='<?php echo $e->escapeHtmlAttr($className) ?>'>hello</div>
<script>var some = '<?php echo $e->escapeJs($javascriptText) ?>'</script>
</body>
</html>
Which produces the following: 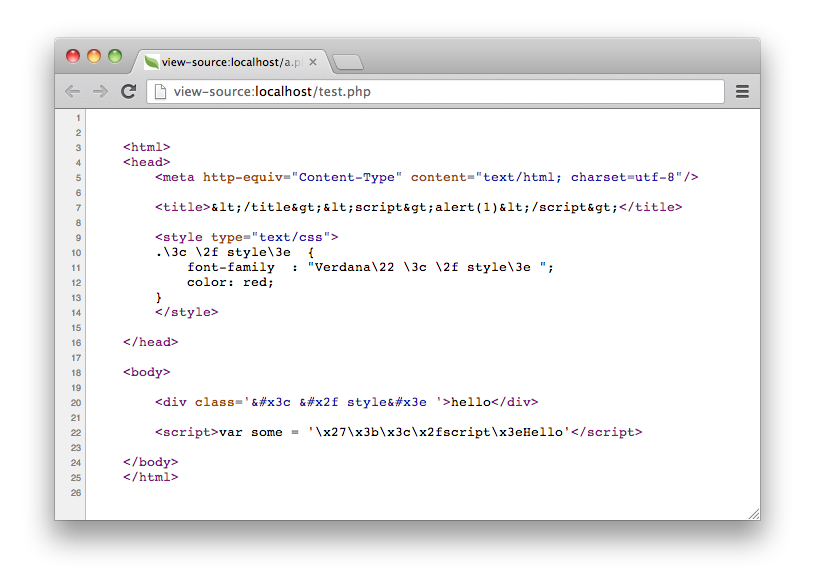
Every text was escaped according to its context. Use the appropriate context is important to avoid XSS attacks. HTML 编码(Escaping HTML)¶The most common situation when inserting unsafe data is between HTML tags: <div class="comments"><!-- Escape untrusted data here! --></div>
You can escape those data using the escapeHtml method: <div class="comments"><?php echo $e->escapeHtml('></div><h1>myattack</h1>'); ?></div>
Which produces: <div class="comments">></div><h1>myattack</h1></div>
HTML 属性编码(Escaping HTML Attributes)¶Escape HTML attributes is different from escape a full HTML content. The escape works by changing every non-alphanumeric character to the form. This kind of escaping is intended to most simpler attributes excluding complex ones like ‘href’ or ‘url’: <table width="Escape untrusted data here!"><tr><td>Hello</td></tr></table>
You can escape an HTML attribute by using the escapeHtmlAttr method: <table width="<?php echo $e->escapeHtmlAttr('"><h1>Hello</table'); ?>"><tr><td>Hello</td></tr></table>
Which produces: <table width=""><h1>Hello</table"><tr><td>Hello</td></tr></table>
URL 编码(Escaping URLs)¶Some HTML attributes like ‘href’ or ‘url’ need to be escaped differently: <a href="Escape untrusted data here!">Some link</a>
You can escape an HTML attribute by using the escapeUrl method: <a href="<?php echo $e->escapeUrl('"><script>alert(1)</script><a href="#'); ?>">Some link</a>
Which produces: <a href="%22%3E%3Cscript%3Ealert%281%29%3C%2Fscript%3E%3Ca%20href%3D%22%23">Some link</a>
CSS 编码(Escaping CSS)¶CSS identifiers/values can be escaped too: <a style="color: Escape unstrusted data here">Some link</a>
You can escape an HTML attribute by using the escapeCss method: <a style="color: <?php echo $e->escapeCss('"><script>alert(1)</script><a href="#'); ?>">Some link</a>
Which produces: <a style="color: \22 \3e \3c script\3e alert\28 1\29 \3c \2f script\3e \3c a\20 href\3d \22 \23 ">Some link</a>
Javascript 编码(Escaping Javascript)¶Strings to be inserted into javascript code also must be properly escaped: <script>document.title = 'Escape untrusted data here'</script>
You can escape an HTML attribute by using the escapeJs method: <script>document.title = '<?php echo $e->escapejs("'; alert(100); var x='"); ?>'</script>
<script>document.title = '\x27; alert(100); var x\x3d\x27'</script>
|